2 Pinterest-styled Free WordPress Themes
Ever since I made this new blog I’ve been digging around for a great free WordPress themes. Currently I’m in love with the design of Pinterest and I want my site to adapt the principle of Responsive design since I use many devices with various screen sizes and orientations. By far, I’ve came across these two great and beautiful themes the Pinboard by One Designs and Sampression Lite by Sampression. More…
Google ID – How to Get It
You want to share your Google ID somewhere? in your web sites or blogs maybe? You still have no idea how to get your Google ID? I’ll show you how to get it. First, go to your Google account page by clicking on your profile picture at the top right corner of any Google page you open then click View profile. More…
SSH Security Improvement
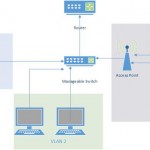
Secure Shell (SSH) is a very handy network protocol which a network/system administrator might use all the time. SSH provides us with the capabilities of data communication, remote login and remote command execution. As a network/system administrator we might be faced with the responsibilities of managing a large amount of server computers. Imagine the pains we would suffer if we have to keep moving around and connecting monitor and keyboard (if we have more computers than monitors) from one computer to another every time we have to manage them. To make our life easier, we can use the SSH protocol with the concept of client server between computers connected on the same network. We just need to run SSH server service on the server side and use our SSH client to do our job from our workstation. More…
Web Server Set Up in Linux and Windows
This is an easy to follow guide on how to set up your computer system as a web server in both Linux and Windows OS. First, we need to setup your system with a web server, MySQL database server and PHP support. here is how to install it in your machine. More…
apache, mysql, php, web server, xampp
Vulnerable Web Application for Hacking
Are you a newbie in hacking world? Want to practice your hacking skills? The biggest problem I’ve faced every time I want to learn about hacking other than it’s not easy to learn the tools is I have a difficult time trying to find a victim for my practice sessions. Surely I can’t try to hack any sites I found on google since it will be against the law. Should I try to make a custom web application for this? Nah, it’s too time consuming and I’m not sure everything will work. Luckily, somehow I found myself in a web page which contain a link to a web application based on PHP and MySQL called mutillidae. More…
Cross Site Scripting, hacking, honeypot, mysql, php, Remote File Inclusion, RFI, SQLi, vulnerable, web app, XSS
SQL Injection
High Interaction Honeypot Analysis Toolkit
High Interaction Honeypot Analysis Toolkit (HIHAT) is a software with the capability of turning any PHP application such as phpmyadmin or phpnuke into a high interaction honeypot. HIHAT works by adding it’s own PHP code into all existing PHP pages/scripts of the application. These generate code were meant to provide logging of every connection attempt to the PHP pages by storing connection detail in MySQL database. HIHAT can handle many types of web security attacks such as SQL injection, Remote File Inclusion (RFI), and Cross Site Scripting (XSS). More…
Cross Site Scripting, honeypot, mysql, php, Remote File Inclusion, RFI, SQL injection, SQLi, XSS